Steganos II Security Suite
Trial
by meRlin 7 April 2000
Published by +Tsehp April 2000
Introduction!
meRlinís tutorial nr: 1
A word from the author:
With Steganos II Security Suite you have chosen a security system that goes far beyond everything you may have used on your PC. Steganos II Security Suite is a total security solution. Hackers and security experts who attempted to break Steganos' encryption failed although tremendous efforts have been made.
Protection is:
Serialnumber registration within
30 days,
if itís not registered before the trial-limit is passed, the OK button is "grayed"
and you must register to run it.
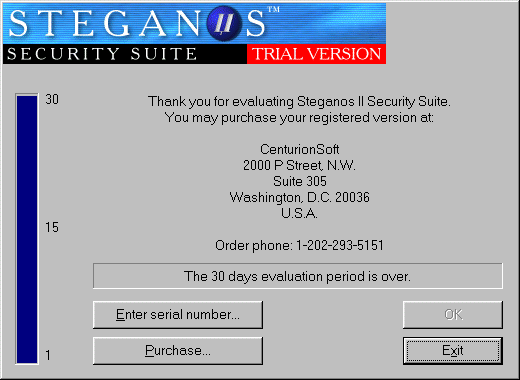
The mission:
Remove the nag and bypass timelimitToolís used:
Softice 4.x
Target:
URL: http://www.steganography.com
Getting started:
I assume you can load files in softice
and also put breakpoints at some places where needed.
When you first start Steganos the "Register-Try" nag is shown, push
OK to run it. Click on "Components" in the menu and select "Shredder"
,
the nag again, test all other options available in same menu,
nag is coming up afteryou have choosen "Safe, Shredder, Sys Lock and Zero
Emission Pad".
Ok so all this items use the same
nag!!
Look in the folder where you installed Steganos, there is separate exeís to
run our items.
Close steganos if still running!
Run each exe in filemon and look for a file used by all of them, hmm to me it
lookís like it is Authorize.dll.
Letís check it out! Load Authorize.dll into Wdasm and take a look at String
Data References, scroll down ohh!! itís all there:
"Thank you for your Registration","Today is day %i of %i evaluation"
Ok thatís all we need to know!!
Finding the nag:
Load Steganos2.exe in softice symbol-loader.Before you push OK button at "Symbol Translation/Load Error" ctrl+d to get to softice and: BPX GetWindowText then push F5 and softice will break at our breakpoint,
Now push F12 one time, you are now
looking at this code:
:014D77D3 push eax
:XXXX77D4 Lea eax, [ebp-0100]
:XXXX77DA push eax
:XXXX77DB push dword ptr [ebp+08]
:XXXX77DE call [user32!GetWindowTextA]
:XXXX77E4 cmp eax, esi ----------------------------You land here
:XXXX77E6 jnz 014D77FC
!! offset can differ from yourís, but the last 4 is always the same (this is only in Authorize.dll)!!
Do: BC * to clear all breakpoints,
push F12 seven times
You are now standing at the line 014D3562 look a few lines above and this is
what you see:
:014D3550 call 014D5A04
:XXXX3555 test eax, eax
:XXXX3557 je 014D3566
:XXXX3559 push 00
:XXXX355B mov ecx, esi
:XXXX355D call 014D5793
:XXXX 3562 test eax, eax---------------------You land here
do BPX DS:014D3550 call 014D5A04
and BPX DS:014D3557 je 014D3566
now step with F10 to do the jump and over call 014D60DA and three lines down
a jz xxxx???? to a push 01
hmm! Ok push F5,
push exit when the nag is shown. Run Steganos2.exe again, softice breaks:
:014D3550 call 014D5A04--------------Here
:XXXX3555 test eax, eax
:XXXX3557 jz 014D3566
we want to change the flow, to force program not to do the jump at :014D3557
jz 014D3566
step down (F10) to the line and: R FL Z +return
now push F5!!
Look the nag is gone ;-)
Running any of the other exeís we
know using Authorize.dll, softice will break again at same place!
Thatís really good because we now know that there is only one place to patch
Authorize.dll
Make the patch and then come back reading.
(several ways to make the patch eg, xor al, al at:014D3555 or at:xxxx3557 jnz 014D3566 or just jmp xxxx3566 do whatever you like !!)
Ready??
Clear all breakpoints in softice, ctrl+d to get there and do BC * +return and
ctrl+d to get back to windows.
Remove Timelimit:
Put the date forward one year or
so and run Steganos. Nothing happens ;-(
Now we load Steganos2.exe into WDasm and do a search Ė>exitprocess
This is the hitís:
:00437974
:00437980
:00437F22
:00462313
:0046456C
standing at the last hit trace back
a bit and take a look, do we have anything intresting here? Maybe!
Look at all the other too.
I think it is the one at :00473F22 because if you scroll up one page or so you
have a LoadIcon event
and at :00437EFF test al, al , and if itís equal =jump over ExitProcess at :00473F22
We can test our taughs, ctrl+d to
softice and: BPX DS:00473EFF and run Steganos when softice breaks!
Look at al (=1) Step one time (F8) and: R FL Z +return and then push F5!!
Timelimit is gone ;-)
To do the crack I change :00437EFB
8A44213 mov al, [esp+13]
:00437EFF 84C0 test al, al
To 33C0 Xor eax, eax ,
FEC0 inc al
FEC8 dec al.
In this way AL is always 0 and it doesenít matter if the date is changed
Steganos2.exe will now run forever.
We still need to do some work on
the other exe files, they use the same type of timecheck.
Load Safe.exe into WDasm, search exitprocess, the first hit at:
00408FBA and look above at 00408FB4
a test bl, bl
And one page up LoadIcon function ;-)
Softice Safe.exe : BPX at DS:00408FB4 then F5 to run, when softice breaks :
R BL 0 +return and push F5!!
OK itís cracked ;-)
The patch: 32DB xor bl, bl
Load Shredder.exe into WDasm and search "exitprocess", this one is slighty different, the result of the checking is made at :
00403D93 84DB test bl, bl
00403D95 7404 je 00403D9B
The crack change 84DB to 32DB xor bl, bl
Test it in softice if you want! (itís working ;-)
If you look carefully there is one
thing that are the same in all files we want to crack except for Shredder.exe!
you can search for afy_s2 and smack land right where this compare is
done.
Syslock.exe in WDasm search
afy_s2 and scroll down to the next ExitProcess, look a few lines up 85D2 test
edx, edx
Softice syslock.exe and : BPX DS:0040E513 , when softice breaks: R DL 0 +return
then push F5!!
The crack 85D2 to 32D2 xor dl, dl
The last one Zep.exe you can crack by yourself without any help!!
Final:
I hope the security in "Steganos II Security Suite" is better than the registration protection ;-)Any comments? Send them to send.me.mail@iname.com