|
VBox Builder 4.2, a TRW session
|

Timelock
|
|
26 MAY
1999
|
by
PLUMe
|
|
 |
Courtesy of Fravia's page of
reverse engineering
|
edited
by Fravia+ |
fra_00xx
980526
PLUMe
1100
NA
PC
|
Interesting stuff (well Timelock protections are ALWAYS interesting). I changed the wording a little, hope PLUMe
will agree with my editing. I also agree about TRW being an useful tool:
TRW
is a very good tool, yet somehow underestimated by the cracking and Fravias communities.
You can learn some basic
usage approaches redaing this essay of PLUMe
(P.S. PLUMe did curiously choose nothing less than
Phrozen's crackme as carrier... I hope that Kc and all other friends there
will enjoy this
involontary publicity for their group :-)
|
|
|
There is a crack, a crack in everything
That's how the light gets in
| |
|
Rating
|
(x)Beginner
(x)Intermediate ( )Advanced ( )Expert
|
|
An essay for beginner
and intermediate Fravias, who can learn an interesting "time activated" protection.
Plus, some nice info about the TRW execution patterns. Advanced readers can of course proceed and
fully reverse
the application if needed.(I'm sure you'll find a more elegant method to patch
Vbox builder 4.2 if you deem it necessary, I just wanted to highlight some aspects of this
interesting protection that can be defeated using TRW).
TRW
is a very good tool, yet somehow underestimated by the cracking and Fravias communities.
You can learn some basic
usage approaches redaing this essay of mine
VBox Builder 4.2, a TRW session
Written by PLUMe
Some days ago, I
read an essay by Master +Xoanon. It is
a very good essay and I wanted to understand better the target's protection scheme,
So I went to
http://www.previewsoftware.com and
downloaded VBox. But I found there a new version. It is
quite different from the target +Xoanon worked on. As it happens, per coincidence, someday ago
I also got a new tool. Well, this tool did permit me to know more about
VBox. What
new tool? You may ask. You may have already heard of TR&TRW.It is a wonderful debugger provided by Liutaotao.I
could't say have much I like it.Vboxt410.dll can not find TRW at all.I could't give
you a patch for VBox.I just can tell Vbox how to work.
TR for windows(version 0.72;You know that Vbox 4.2 has its anti-softice and other
debugger routines)
TR for Win95/98(TRW) is a great debugger running in Win95/98. TRW can trace DOS COM, DOS
EXE, DOS protected mode, 16bit NE, 32bit PE applications, and trace ring 0 kernel
VxD. TRW run in Win95, OSR2, Win98. ttp://www.netease.com/~ayliutt
SoftIce (we need it always)
Mkpe(1.30)
VBox
Builder (a tool to add Vbox to your programs, very useful for cracking purposes
too, eh eh)
TimeLock by PreviewSoft has long and glorious history (of its cracking: Timelock has always been a 'worthy' protection
scheme). Vbox is "a new beginning" of a kind. It's different
from its predecessors almost to the loss of any ancestorial resemblance.
First of all, install the VBox builder (you need to get a .prv file from their
webserver, so connect to the internet for this and fill the form needed). Then
choose a .EXE file to protect (you could choose also a .DLL or an .OCX, but
choose an .EXE coz it's better and easier for cracking purposes.I choose
Official phrozen crew trial crackme) and wrap it
with VBox using the builder (choose now the Trial days protection).
Now the fun begins. And as we can easily see, the whole VBox protection scheme
consist of only
one dll which is copied into your \WINDOWS\VBox\command directories. The name of our
target DLL
is vboxt402.dll. It is packed.
Step 1:
Here I'll show you how to use TRW.
Run TRW,select "hide" button.
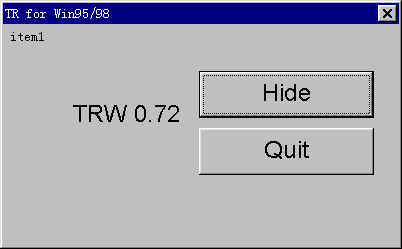
Then a green icon appear at right corner.
You can hit right button on it.It appear like that.
Step 2: Let's change time to 30 days later.Now you can run crackme.exe.When
VBox window appear.CTRL-N,enter TRW.You can use "hwnd" find VBox window's
hwnd.Something like xxxx.
bpmsg xxxx wm_destroy;
just like in softice.
g; come back to VBox.
Press "quit" button.
Now you are in TRW.
bc *;clear break point.
press F12 a few times.Until you come here in vboxt402.dll.
07006079: call [dword dialogparama]
0700607f: mov esi,eax; If
you press "try" eax=0,if you press "quit" eax=1; so change
eax to 0. r eax 0.
There have some others check.
07001c03: cmp [ebp-10],eax; If eax=[ebp-10],error
dialog will appear.So change eax .
07001c06: jne 07001c2c
07001c08: lea eax,[ebp+10]
07001c0b: lea ecx,[ebp-74]
07001c0e: push eax
07001c0f: mov [ebp-78],ebx
07001c12: call 0702e7d0
07001c17: lea eax,[ebp-7c]
07001c1a: push 07070568
07001c1f: push eax
07001c20: mov [dword ebp-7c],0706e004
07001c27: call 070570a0
07001c2c: lea ecx,[ebp-28]
07001c2f: mov [byte ebp-040,04
07001c2c: lea ecx,[ebp-28]
07001c2f: mov [byte ebp-04],04
07001c33: call 0702d440
07001c38: lea ecx,[ebp-18]
07001c3b: mov [byte ebp-04],02
07001c3f: call 0702d440
........
07001c7c: call 07032570
07001c71: cmp [ebp-10],eax; Another check.
07001c74: jne 07001f9b; If
eax=[ebp-10],error dialog will appear. So change eax.
Ok, now theoretically our patch is done....
1.07006079: call [dword dialogparama] patch to
07006079: xor eax,eax
0700607b: nop
0700607c: nop
0700607d: nop
0700607e: nop
2.07001c06: jne 07001c2c to 07001c06:jmp 07001c2c
3.07001c74: jne 07001f9b to 07001c74:jmp 07001f9b
VBox screen will not appear anymore BUT: we just did it in memory, that's not permanent,
as you all know very well... We must now apply our patch
on the real file. But vboxt403.dll is packed?
Step 3:
Close TRW. (TRW's bpm function doesn't seem to work there)
Let run softice.(Vbox Unpacked code firstly,then check softice)
load crackme.exe
bpm xxxx: 07006079 w;
Ok, so set this breakpoint and rerun. You will land in vboxt410.dll
here:
009c01b7: repz movsd
009c01b9: mov ecx,edx
009c01bb: and ecx,03
..........
Oh!My GOD!! It is encrypted before running. Therefore you could't
find these code inside
vboxt410.dll.
bpm xxxx: 009c01b7 w;
so set this breakpoint and rerun.You will land in here:
00a001b7:repz movsd
00a001b9:mov ecx,edx
00a001bb:and ecx,03
..............
Try again.
bpm xxxx:00a001b7 w;
so set this breakpoint and rerun.You will land in here:
07093c27:mov [edi],al
07093c23:inc edi
07093c24:inc ebp
........
Try again.
bpm xxxx:070093c27 w;
so set this breakpoint and rerun.You will land in here:
| :07093422 03D0 add edx, eax |
| :07093424 C1E902 shr ecx, 02 |
| :07093427 F3 repz |
| :07093428 A5 movsd; here!!! |
| :07093429 8BCD mov ecx, ebp |
| :0709342B 89542414 mov dword ptr [esp+14], edx |
| :0709342F 83E103 and ecx, 00000003 |
| :07093432 F3 repz |
| :07093433 A4 movsb |
| :07093434 8B4344 mov eax, dword ptr [ebx+44] |
Yes,you can find these code in vboxt410.dll.
It is almost same when you bpm xxxx:07001c06
or bpm xxxx:07001c74.
Frankly, I did not find an elegant way to patch it. It modifies itself quite a lot.
If find an elegant way to patch it, please let me know.
|
Now I try to get a clean routine using another
approach.
But it does not always
work, beware! |
So let's forget for a while our vboxt402.dll. We just want a clean routine.
Run TRW.
Change eax at: .
1.07006079: call [dword dialogparama]
2.07001c06: jne 07001c2c
3.07001c74: jne 07001f9b
So I just run
our "Official phrozen crew trial crackme" a window
pop-up.press "ok", enter it's main routine window.
Now find its hwnd (you know how to do this, I hope :-),
and then just bpmsg
on it inside TRW.
Now: g; go back to
phrozen's window,press "exit" .
Just like before TRW pop-up. Press F12 as long as needed to find the relevant code...
00401029: push 00
00401030: push 00401046
00401032: push 00
00401034: push 01
0040103a: push dword 0402dd87
0040103f: call 00401313
00401041: push 00; you land here
00401046: call 0040127d
........:............
You can go to xxxx:00401029 directly and dump it from memory using
"pedump"
command.
Then you get dump1.exe.
MKPE dump1.exe -a -s -f -i3 -ldlllist.sam
Fileout.exe is our "clean" routine, and it works very well.
So: byebye VBox Builder 4.2.
As you can now see -once more- commercial ready-made protections are not so secure as they claim
(look at http://www.previewsoftware.com
.)
But at times my fileout.exe approach does not work. I wonder way... unfortunately
I did not find any clear
patterns to reverse this little mistery. If you understand this, or if you have
any other good methods for this target, please
let me know, we will modify together this essay.
<plume(at)kail(dot)com.cn>
I wont even bother explaining you
that you should BUY this target program if you intend to use it for a longer
period than the allowed one. Should you want
to STEAL this software instead, you don't need to crack its protection
scheme at all: you'll
find it on most Warez sites, complete and already regged, farewell.
You are deep inside Fravia's page of reverse engineering,
choose your way out:

Timelock
 homepage
homepage
 links
links
 search_forms
search_forms
 +ORC
+ORC
 students' essays
students' essays
 academy database
academy database
 reality cracking
reality cracking
 how to search
how to search
 javascript wars
javascript wars
 tools
tools
 anonymity academy
anonymity academy
 cocktails
cocktails
 antismut CGI-scripts
antismut CGI-scripts
 mail_Fravia
mail_Fravia
 Is reverse engineering legal?
Is reverse engineering legal?


